This image was made by hand, using data available from previous network analysis.
This entry was awarded second prize in the 2012 IPv6 Challenge during the World IPv6 Launch in Amsterdam.
Stateless automatically configured IPv6 addresses consist of two parts: a 64 bit network identifier and a 64 host identifier. The prefix uniquely identifies the network and the suffix uniquely identifies the device within that network.
However, as specified in RFC 4862, the host identifier is generated using the device's hardware address, or MAC, which means that it isn't just unique within the current network, but likely to be unique across the entire internet. And not just unique: it'll remain the same, even as you switch between networks.
So, consider for instance three networks:
By actively engaging in network communication to all of these addresses and examining the difference between the results, it might be possible to determine to which network the mobile device is currently connected.
The simplest example of this would be to send an ICMP echo request, or "ping", and watch if a echo reply is returned.
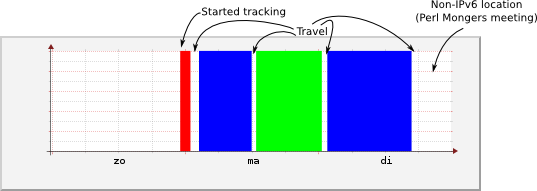
Whenever a computer is connected to a certain network, it's often easy to determine its location, since networks are often location bound.
For example, I have been tracking my own location using this technique. This was possible because I visit three locations that have an IPv6 enabled WiFi network:

This image was made by hand, using data available from previous network analysis.
Generic automated network monitoring utilities can also be used for this purpose. This is an example of one specific network/host-combination. I don't know who this is, but it's someone who has previously visited ip6.nl :-)
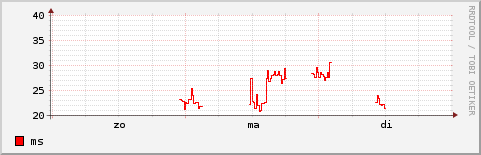
Combine several of these charts using different colors for different networks, ignore the actual values in the chart, and a location pattern emerges.
Using something like Nagios, it's even possible to send out SMS notifications ;-).
Being able to track someone's location is a huge violation of privacy. Fortunately, it is often possible to enable Privacy Extensions, as defined in RFC 4941. Once enabled, these cause a random host identifier to be generated, a new one on every network, and even a new one each time a preset period of time elapses. Privacy Extensions make gathering EUI-64 (hardware address based) host identifiers rather hard.
However, the Privacy Extenions will not disable the non-random host identifier. If one was obtained before the extensions were enabled, or by other means, the addresses can still be used for tracking one's location.
Other ways of obtaining MAC addresses, from which the equivalent EUI-64 addresses can easily be constructed:
To fully prevent the EUI-64 address from being used, a firewall is required. One naïve approach in Linux would be:
ip6tables -A OUTPUT -s fe80::/ffff:: -j ACCEPT ip6tables -A OUTPUT -s ::ff:fe00:0/::ff:ff00:0 -j DROPThis ruleset will prevent the use of EUI-64 addresses outside the local network, effectively ensuring that it cannot be used from the internet. With Privacy Extensions enabled, normal outgoing network traffic will continue to work using the randomly generated addresses.
In my opinion, it would be a good idea if operating systems disabled the EUI-64 addresses when Privacy Extensions are enabled, to properly guard one's privacy. Most current versions operating systems have Privacy Extensions enabled by default, but as described in this document, this is not good enough.
(It has been brought to my attention that OpenBSD already does this.)
Juerd Waalboer <juerd@tnx.nl>
World IPv6 Launch, Amsterdam, 2012-06-06